It is common for businesses that provide online accounts or mobile apps to ask for phone numbers to verify new users through SMS PIN codes. The main reason, among many other benefits, is that SMS, with its high reach, makes it super convenient for users to verify their identity via their cellphone number.
They're turning to the same technology for two-factor authentication (2FA) – sending an SMS PIN code every time a user logs into an account, whether from a web browser or an app.
We've covered the need to implement 2FA as a security feature in the past, and the need to have it in place in light of the new EU regulations is rather evident. One of its most important aspects is balancing user-friendliness and security. That is where the good old SMS shines through. We'll also talk about an additional step for security: using an authenticator app.
When and where you need user authentication
At this point, we've all surely experienced user authentication in some shape or form. Be it downloading a popular OTT app such as Viber or Whatsapp, performing banking transactions online, or even voting if you live here in Estonia.
These days, most applications require more than a single password, and two-factor authentication can involve using different types of security keys:
Something the user already knows (for example, a chosen password)
Something the user has (for example, unique biometric data such as fingerprints)
Something the user gets (for example, a PIN code sent in an SMS message)
A combination of these significantly increases security, and SMS is an easy, reliable, and straightforward way to deliver your authentication notifications as a second layer. So, it's great to ask for passwords along with one-time codes that are sent to mobile phones.
How SMS two-factor authentication works
The SMS authentication process is pretty straightforward. The user enters the mobile phone number into the application's form, receives an authentication PIN code via an SMS message and types it into the application's form to confirm their identity and gain access to their account and info.
For added security, a flash SMS can be used, which is a type of SMS that shows up on the recipient's screen for one-time viewing instead of being sent into the SMS inbox. This means the security code is not stored on the recipient's handset, adding another piece of security via mitigated storage.
Key factors that make SMS a great 2FA tool
There are three main reasons why SMS authentication works for both businesses and their customers.
It's fast
An SMS notification can be received on a handset super quickly. It won't get in the recipient's way or slow them down. With the "within seconds" delivery, you can be assured that users won't retry immediately either, which mitigates the costs of delivering SMS authentication codes since each retry could add to the cost.
It's easy
SMS authentication can be set up with the same SMS API you use to communicate with your customers for marketing purposes. Thus, it is easy to set up.
Most users are already familiar with how text message notifications work. The process is very straightforward and intuitive. There is no need for users to install any additional apps or extensions either. Thus, this authentication method is simple for your users too.
It's secure
The SMS notification is generated and sent offline via the cell network, not email or the web. The application can compare the originally generated authentication code with the one the user types in. This reduces the chances of in-transit interception.
There are some concerns about other types of security risks, of course. The matter has been blown a bit out of proportion, though, as the methods for interception are still somewhat challenging to deploy and super rare in actuality.
If you use SMS as an OOB (out-of-band) channel for 2FA, consider an additional knowledge factor to secure the account or payment further. That will provide extra security against certain SIM swapping or SMS interception scenarios, should they occur.
An extra step: Gain access with a 2FA app
2FA mobile apps, such as Google Authenticator, don't use SMS PIN codes for two-factor authentication. Instead, they use six-digit one-time passwords that expire after a specific time, usually 30-60 seconds.
These time-based one-time passwords (TOTP) are calculated independently by both the authenticator app and the service you are logging into, so they are safe from the SS7 vulnerabilities that have put SMS under scrutiny.
Only the user-entered TOTP is transmitted to the API by the online service in question, as the online service checks with the API if the correct TOTP was entered before access is granted.
The independent generation of the TOTPs means that there is a transmission of limited data and, thus, a smaller chance for anyone to intercept the code. This makes the system safer by simply limiting data delivery.
Onboarding users to the authenticator app
Let's consider Google's authenticator app to demonstrate our onboarding example since it is one of the most commonly used two-factor authentication apps. The process might differ for other services, but the inner workings are pretty much the same.
To start, the user must first install the Authenticator app on their iOS or Android device. It's absolutely free!
The next step involves scanning a QR code to add a user account for a specific third-party service. This QR code is displayed on the third-party website that you are logging into.
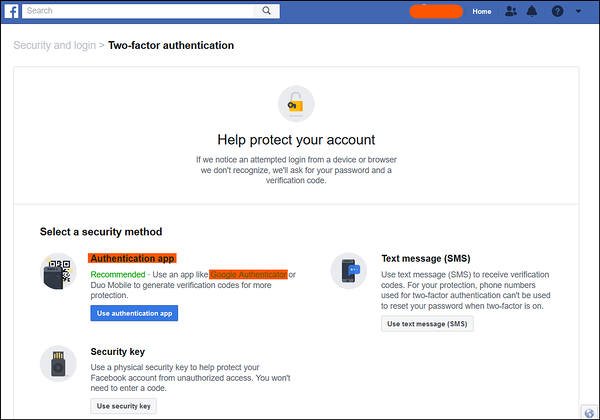
For example, let's suppose you want to set up Google Authenticator for your Facebook login process. You will first have to enable 2FA from your Facebook settings.
It will show you a QR code that is to be scanned via the Google Authenticator app on your phone. This will set up a system for all future logins to your Facebook account, essentially "adding" Facebook to your Authenticator app. You can do the same for any other service that offers 2FA via Google Authenticator, such as Gmail or WordPress.
For future uses, no scanning of QR codes or any other steps will be needed. You will simply have to enter your password on Facebook, open the Authenticator app, check the 6-digit code under 'Facebook', and enter this code into the Facebook 2FA textbox.
Some authenticator apps also send push notifications to users when they log in, so they don't have to search for the account in the app. This makes it easier to use on a daily basis than an SMS-based system. Push notifications tend to be a bit quicker in arriving than text messages as well.
Wrapping up
So, there you have it. SMS 2FA is a simple and secure way to add more in the way of security to your users as well as improve the compliance of the company in question. If you're already using SMS PIN codes to authenticate users every time they log in, you can improve it by supplementing it with a third-party authenticator app to add an extra layer of protection.