As data protection has and continues to become more and more of a hot topic, both in the legislative field via major regulations such as the GDPR and PSD2, as well as in the media via more commonly occurring data breaches and fraud, it’s important to do our best to keep the data safe.
While communication encryption between partners and operators, as well as a technical standard application such as using an HTTPS protocol is managed from the SMS API provider's side, there is more that can be done by the sender as well.
Wish to know more? Here's everything you need to know about SMS API providers!
To ensure confidentiality, the content of each SMS message sent can be “hashed” (meaning that the content is in an illegible format that can only be read at the end customers end, with 256bit encryption used) and “no-stored” (the content is not stored in the databases of the service provider and is thus not viewable).
Both the content hashing and the no-store feature hide the original content on the dashboard, reports and in our internal logs so no prying eyes (administrators, account users, the team at Messente) can see the information that has been sent.
The origination of these features came from the request from one of our customers - a credit card provider. The need to deliver PIN codes or critical information on credit statuses requires them to keep a high level of confidentiality. The team at Messente is not and shouldn’t be privy to that kind of information. Thus, these options help protect the customers and the senders.
The content no-store API request would look similar to the following URL when generated by our API library:
https://api2.messente.com/send_sms/?username=...&password=...&to=%2B372...&text=Test&text-store=nostore&time_to_send=&from=…
The API request for content hashing, also a URL generated by our API library, will look like:
https://api2.messente.com/send_sms/?username=...&password=...&to=%2B372...&text=Test&text-store=sha256&time_to_send=&from=…
The “store=nostore” and “store=sha256” parameters illustrate the use of the content protection methods.
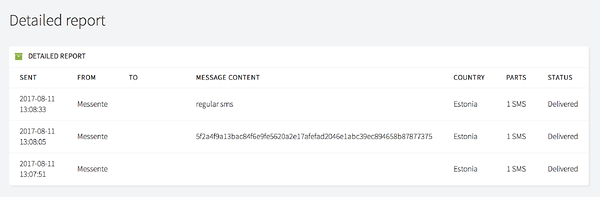
The following photo displays the content on the dashboard. The first message is a regular SMS, the second is hashed one, and the third is a no-store SMS.
Conclusion
Using these methods ensures that confidential content can be hidden from both the dashboard and reports. Combined with Flash SMS, the content doesn’t exist anywhere besides on the sender’s side initially and in the user’s memory once they see the Flash SMS.
This way, any sensitive information can be sent in a secure way, keeping passwords, PIN codes, and secret wishes from any and all deviants looking to exploit the data for fraud, identity theft or any other wrongdoing.