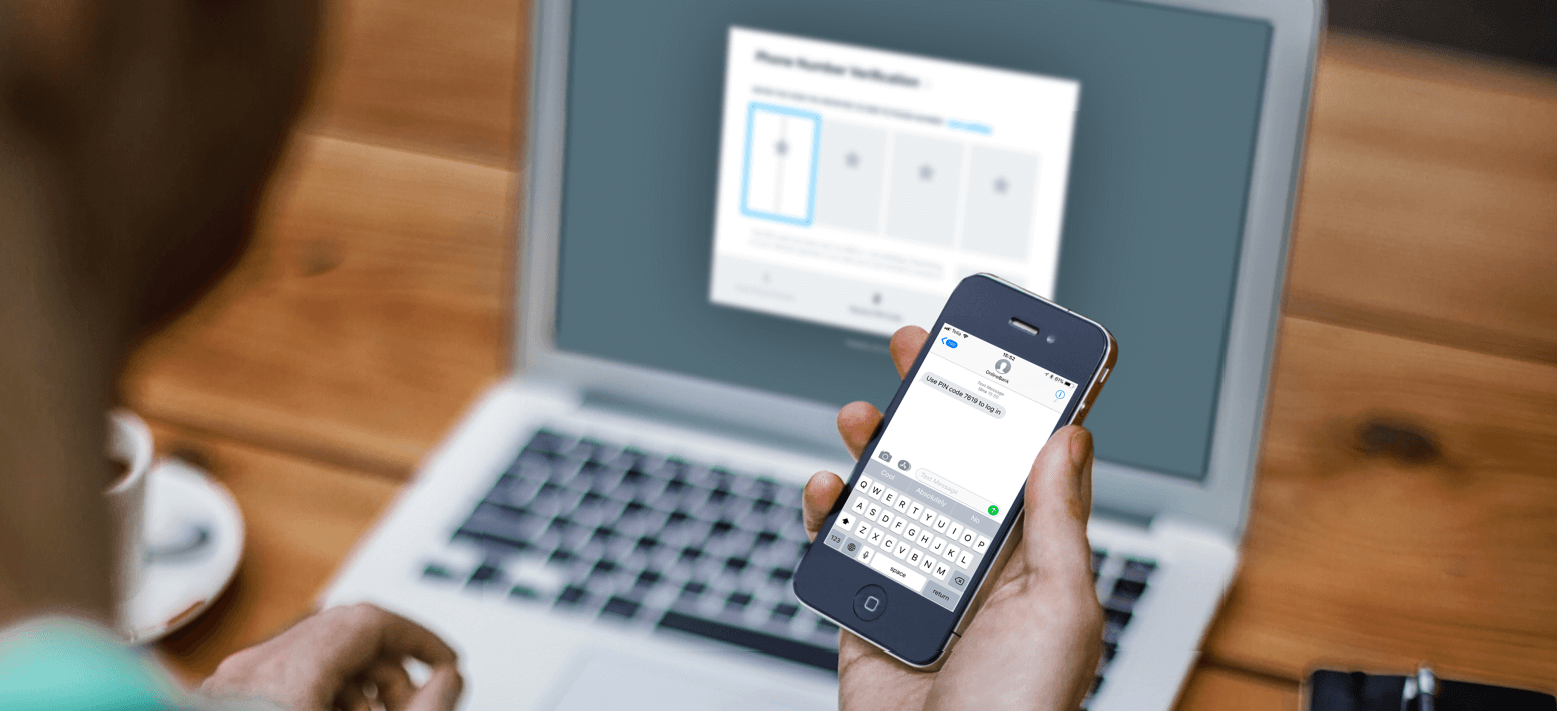
An alternative would be to include an URL along
with the security code in the SMS message. The URL would be linked with encrypted transaction information - accessible via something the user knows, as well as the security code (received on something the user possesses).
SMS is an easy option for account and payment verification
SMS as used for both account and payment verification is known as an Out-of-Band option (OOB). It’s the easiest and most popular method to consumers and is fully compliant with the rules for Account Access and should be an option for Payments if the payment information is included in the SMS. It also meets the requirement of channel independence.
Of course, these days, there are some security issues with SMS. However, many of these are somewhat overblown in the press (e.g. SIM-swap, SMS interceptions). If using SMS as an OOB channel for two-factor authentication, consider adding an additional knowledge factor to further secure the account or payment. That will provide extra security against certain SIM-swap or SMS-interception scenarios, should they occur.
These are just two practical examples of what
RTS has brought to the table and a tool that can help with the account and
payment verification management - SMS. There are many more to come though, and
we’ll cover additional ones in more detail in our blog.